Cryptocurrency security is more criIn 2025, crypto security isn’t optional — it’s survival.
Hackers are using AI-powered phishing, deepfake support scams, and new malware to drain wallets faster than ever. Whether you hold Bitcoin, Ethereum, or new AI agent tokens, protecting your assets now means peace of mind later.
This guide shows you exactly how to secure your cryptocurrency — from using the right wallets and backup methods to spotting scams before they strike. By the end, you’ll know the best ways to keep your crypto safe going into 2026 and beyond.
If you’ve already lost access to your crypto, read this next: How to Find Legitimate Crypto Recovery Companies
How to Secure Your Cryptocurrency: Quick Answer
Here’s the short version — your crypto security checklist for 2025:
| Step | Action | Why It Matters |
|---|---|---|
| 1. Use a Hardware Wallet | Move funds offline with trusted devices like Ledger Nano X or Trezor Safe 3. | Keeps your private keys away from hackers and malware. |
| 2. Enable Two-Factor Authentication (2FA) or Passkeys | Use app-based 2FA or a FIDO2 security key instead of SMS. | Protects against SIM-swap and phishing attacks. |
| 3. Back Up Recovery Phrases Securely | Write seed phrases on paper or metal, and store them offline in separate safe places. | Prevents total loss if your wallet or device fails. |
| 4. Beware of Phishing & Deepfakes | Always double-check URLs and never share private keys or “verification codes.” | AI scams in 2025 mimic real exchange support agents. |
| 5. Keep Devices & Wallet Firmware Updated | Regularly update your exchange apps, wallets, and security software. | Fixes vulnerabilities before hackers can exploit them. |
| 6. Audit Your Security Every Quarter | Review passwords, backups, and 2FA settings. | Ensures you stay protected as threats evolve. |
| 7. Learn & Adapt | Stay informed through trusted crypto news and official security blogs. | The more you know, the harder you are to hack. |
Pro Tip: Keep only small amounts in hot wallets for trading or daily use. Store the rest safely offline in cold storage.
Top 5 Must-Do Steps to Secure Your Cryptocurrency (2025 Edition)
Crypto security in 2025 isn’t about checking boxes — it’s about building a defensive system that evolves faster than new scams. Below are the five real habits separating cautious investors from those who lose everything to a fake support chat.
1. Go Beyond “Hardware Wallets” — Use Multi-Signature Storage
Most people stop at “get a Ledger.” Smart investors go further.
Use multi-signature wallets like Casa or Unchained Capital that require two or three separate keys to approve a transaction.
That means no single wallet, app, or person can move your funds — even if one key is compromised.
Pro insight: Store one key in a hardware device, one on a backup device, and one with a trusted custodian. It’s not paranoid — it’s professional.
To recover your cryptocurrency in case of an attack, consider working with legitimate crypto recovery companies that help users retrieve stolen assets.
2. Ditch SMS 2FA — Use Passkeys or YubiKey Instead
In 2025, SIM swaps and fake “exchange verification” calls are at an all-time high.
Skip text-based 2FA completely. Instead, use FIDO2 passkeys or YubiKeys for login verification.
Passkeys are stored securely in your device’s chip, meaning hackers can’t phish or intercept them.
→ Think of it as a digital fingerprint for your wallet.
3. Encrypt and Fragment Your Recovery Phrase
Writing your seed phrase on paper is outdated. A smarter move is fragmented backups.
Split your 12 or 24 words into 2–3 encrypted pieces (using tools like Cryptosteel Capsule or SLIP39 Shamir backups) and store them in separate physical locations.
If someone finds one piece, it’s useless without the others.
This small layer of complexity frustrates most attackers instantly.
If you’re unsure about which firms to trust for recovery help, read more about crypto recovery firms that don’t charge upfront fees to make sure you’re not scammed.
4. Stop Relying on “Free Wi-Fi” — Segment Your Devices
Many crypto thefts start from an infected phone or laptop.
Keep one dedicated “clean” device for crypto transactions only — no Telegram, no browser extensions, no random app installs.
Better yet, use a separate Wi-Fi network or mobile hotspot just for crypto use.
It’s how pros prevent invisible spyware from logging every keystroke.
5. Run Security Drills Quarterly
This one separates the cautious from the competent.
Every few months, simulate a failure:
- Lost wallet? Test your recovery phrase.
- Device crash? Try restoring your funds on a secondary device.
- Change exchange passwords & 2FA.
- Check that all your wallets are still using the latest firmware.
The goal isn’t perfection — it’s familiarity under pressure.
Reality check: When something goes wrong, panic costs more than the hack. Practice like it’s real.
If you’re navigating volatile markets, it’s also crucial to know how to avoid losing in cryptocurrency trading to protect both your investments and peace of mind.
Emerging Crypto Threats in 2025: What’s Actually Happening Now
Most “crypto security guides” still talk about phishing emails and sketchy exchanges. That’s old news.
The new wave of attacks in 2025 is quieter, faster, and almost impossible to spot — until your wallet’s empty.
Here’s what’s really happening right now.
1. AI-Generated “Recovery Experts” Are the New Exit Scam
They look human, speak like seasoned devs, and even reference your specific transaction hashes — all generated by AI.
These fake “recovery experts” reach out after a wallet drain or NFT theft, promising to “trace and reclaim” your funds for a 5% cut.
You’ll get a fake progress report, a fake transaction preview… and then they disappear.
No hacker needed — just your desperation.
Rule: Never trust anyone who contacts you about recovering funds. There’s no real “crypto recovery service.” Only law enforcement and forensics firms like Chainalysis have the tools, and they don’t DM anyone.
2. Wallet Drainers Masquerading as Airdrops
You don’t even have to click anymore — just viewing a malicious webpage with your wallet connected can trigger a hidden drainer contract.
These are often disguised as “airdrops,” “NFT claim pages,” or even “DeFi re-staking dashboards.”
What’s tricky: they use legit-looking ENS names and verified smart contracts that were later swapped out.
Defense: Never connect your main wallet to anything new. Use a “burner” wallet for all testing or claims — a separate address with nothing valuable inside.
3. Deepfake Support Calls and Exchange Impersonators
Attackers are now using AI voice models to mimic real customer support reps from Binance, Kraken, or Coinbase.
You’ll get a call about a “stuck withdrawal” or “KYC verification.”
They sound identical to official staff and can even reference recent transactions pulled from blockchain explorers.
Tell: They’ll always rush you. Real support teams never call you directly — they email via verified domains.
4. Telegram “Dev” Groups That Install Malware
Many smaller projects on Telegram or Discord now host “beta test” downloads for wallets, dashboards, or bots.
Half of these are Trojan loaders that quietly scrape your clipboard for private keys or wallet addresses.
The catch? They work fine for days before stealing anything.
They wait until your next transaction, then swap your destination address at the last second.
Solution: If it’s not from an official website, don’t install it — ever.
5. Compromised Browser Extensions
Extensions that claim to show “live gas fees,” “token trackers,” or “airdrops” often inject malicious scripts.
A few weeks ago, a Chrome plugin with 40K downloads was caught rewriting MetaMask’s network list.
Even uninstalling it didn’t help — it modified browser-level storage.
Defense: Use one browser for crypto only, and disable all extensions. Brave, Arc, or LibreWolf with network isolation works best.
The takeaway: crypto theft in 2025 doesn’t look like hacking anymore — it looks like trust.
Attackers don’t break your wallet; they borrow your confidence.
In 2022, the Ronin Network (a blockchain gaming platform) was hacked for over $600 million in cryptocurrency. The attackers exploited a weakness in the system’s security architecture, making it a stark reminder of the importance of securing your crypto assets.
To ensure your assets are protected, be sure to stay safe from honeypot scams by following best practices.
When assessing risk, you’ll want to grasp new token mechanics like those in AI agent coins. Here’s a full guide: What Is an AI Agent Coin
Two-Factor Authentication: Why It’s Crucial for Crypto Security
Two-factor authentication (2FA) is a critical first defense against unauthorized access. Even if a hacker gets your password, they’ll also need your 2FA code.
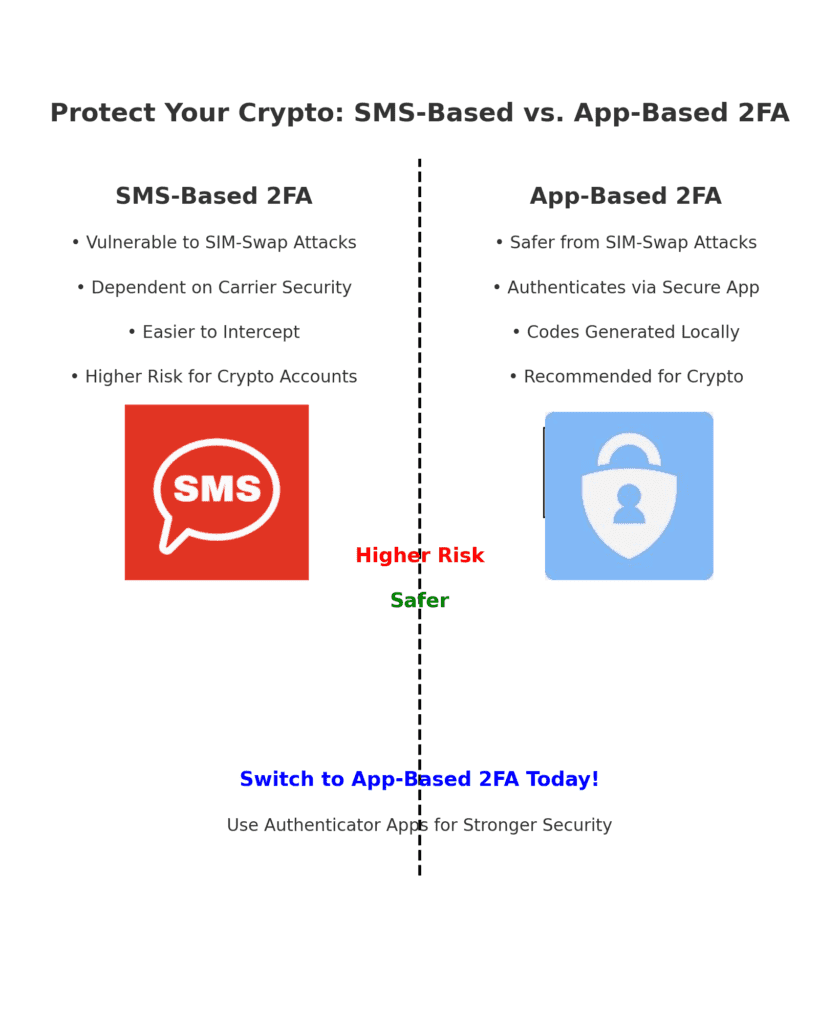
- Actionable Tip: Always use app-based 2FA (like Google Authenticator or Authy). Avoid SMS-based 2FA, as it’s vulnerable to SIM-swapping attacks, where hackers hijack your phone number.
Avoiding Phishing Scams and Fake Websites
Phishing is one of the most common ways people lose their cryptocurrency. Scammers create fake websites that look identical to legitimate crypto exchanges or wallets.
What to Watch For:
- URLs that look almost identical to real ones but have subtle differences (e.g., “coinbasse.com” instead of “coinbase.com”).
- Emails claiming to be from a trusted platform but asking for your login details.
Tip: Always type in the URL yourself or use bookmarks for your most trusted crypto sites.
Even with backups, mistakes happen. Here’s a look at password recovery tools for crypto wallets that can help: Crypto Recovery Software.
.
Advanced Security: Multisig Wallets and Sharded Backups
For those who want extra protection, you can use multisignature (multisig) wallets and sharded backups:
- Multisig wallets require more than one key to authorize a transaction, adding a layer of security. This is particularly useful for businesses or joint accounts.
- Sharded backups allow you to split your recovery phrase into parts and store them in separate locations, reducing the risk of losing access to your funds.
If you’re ready to take your crypto earnings to the next level, consider strategies on how to take profits from crypto without selling while maintaining your long-term positions.
Regular Crypto Security Audits
To maintain top-notch security, it’s important to regularly audit your crypto security setup:
- Check your backup strategies: Make sure your recovery phrases and hardware wallets are still secure.
- Update your passwords and 2FA regularly to stay ahead of evolving threats.
- Review your software: Ensure that all wallets and exchanges you use are up-to-date with the latest security patches.
Case Study: The 2024 Atomic Wallet Hack — What Really Happened
I still remember that weekend in June 2024 when my Twitter (now X) feed exploded with panic posts — hundreds of Atomic Wallet users claiming their coins were gone overnight.
By the time CertiK confirmed the breach, over $100 million in assets — including Bitcoin, Ethereum, and USDT — had vanished.
What Actually Went Wrong
After tracing blockchain reports and community threads on r/CryptoCurrency, it became clear the issue wasn’t just “bad luck.”
Here’s what stood out to me:
Compromised update: Attackers slipped malicious code into Atomic Wallet’s update server. Once users installed it, their private keys were silently exfiltrated.
No hardware isolation: All keys were stored in software memory — no cold storage fallback.
Telemetry leakage: The wallet’s optional data-sharing system gave hackers an unexpected edge in targeting vulnerable installations.
Even worse, Atomic Wallet initially downplayed the scale, and users who hadn’t backed up offline copies of their seeds had zero recovery options.
What You Can Learn (From Someone Who’s Been in the Space Since 2017)
Here’s how I handle self-custody today — and what I wish more people did before they learn the hard way:
Never rely on a single wallet provider.
I split holdings between a Ledger Nano X for long-term storage, and a minimal hot wallet (like Exodus) for everyday swaps.
Verify every update manually.
Bookmark the wallet’s official domain and never update via app store links or community channels. Atomic’s fake Telegram “update” was how many users got drained.
Use metal backups for seed phrases.
A $40 fireproof metal card is better than losing five figures in tokens. Check out community-vetted options like Seedplate (frequently discussed in /r/Bitcoin).
Monitor your addresses.
Tools like DeBank or Zapper help detect unauthorized movements. Set alerts for any unexpected token approvals.
Follow reputable security sources.
I personally track @officer_cia, CertiK, and DeFiSafety for early breach alerts — often hours before major news sites catch up.
Takeaway: Non-custodial doesn’t mean invincible. Atomic Wallet users learned that security doesn’t end when you click “install” — it begins there.
Useful References:
CertiK post-mortem on Atomic Wallet breach
Reddit: r/CryptoCurrency discussion thread on the hack
Ledger’s official “How We Secure Private Keys” whitepaper
Future-Proofing Tip Box: How I’m Preparing for 2026 Crypto Threats
If 2024 was the year of wallet exploits, 2026 will be the year of AI-assisted scams and deepfake social engineering.
I’ve already seen early signs in Discord communities — fake “admin” voice calls that sound shockingly real, tricking users into revealing seed phrases.
Here’s my personal checklist to stay ahead of what’s coming:
Hardware + Passkey Combo (My 2026 Rule).
I now use a YubiKey for 2FA plus a Ledger Stax for offline signing. Even if someone deepfakes my voice, they can’t bypass physical confirmation.
AI Awareness Training.
It sounds corporate, but I make it a point to test myself — could I spot a fake Binance email with AI-written tone? Probably not always. So I verify everything through the URL bar, never by “replying.”
Smart Contract Permission Hygiene.
I run Revoke.cash monthly. You’d be shocked how many dApps hold lingering token approvals from projects you’ve forgotten.
Multi-chain Key Segregation.
I use separate wallets per network — one for Ethereum, one for Solana, one for Bitcoin. Cross-chain bridges will likely be the next weak link.
Offline Backup Rotation.
I rotate physical backups (one metal, one encrypted USB) every six months and store them in separate physical locations.
Future tip: Bookmark Revoke.cash
, Etherscan Approvals
, and the Ledger Academy security hub
— these are your real “safety nets” before AI hackers catch up.
And if you hang out in r/CryptoCurrency or r/ledgerwallet, you’ll notice one theme repeating:
Everyone thinks they’re safe until they’re not. The best investors I know treat wallet security like hygiene — not heroics.
FAQs On Securing Your Cryptocurrency
How do I protect my crypto wallet?
To protect your crypto wallet, use a hardware wallet (cold storage), enable two-factor authentication (2FA), and securely back up your recovery phrase offline. Regularly update your wallet software and be cautious of phishing attacks. Tip: Avoid keeping large amounts of crypto in online wallets (hot storage).
What is the safest crypto wallet?
The safest crypto wallets are hardware wallets like Ledger and Trezor, as they store your assets offline and are nearly immune to hacks. For beginners, these wallets are highly recommended for long-term storage of larger crypto holdings.
How do I make my crypto wallet secure?
You can secure your crypto wallet by using strong passwords, enabling app-based 2FA (like Google Authenticator), and backing up your recovery phrase securely. Keep the phrase offline and avoid digital backups. Pro Tip: Regularly review your security settings and update them.
Does the IRS consider crypto a security?
No, the IRS classifies cryptocurrency as property, not a security. This means crypto transactions are taxed similarly to capital assets like stocks or real estate.
Where is the safest place to keep your cryptocurrency?
The safest options are cold wallets (hardware wallets), which store your crypto offline, protecting it from hacks. Choose wallets from trusted manufacturers and safeguard your recovery phrase.
How do you avoid losing money in crypto?
Research thoroughly before investing.
Use cold wallets for secure storage.
Diversify your investments to spread risk.
Avoid scams and don’t fall for “guaranteed returns.”
Only invest money you can afford to lose.
Can you lose crypto in a cold wallet?
Yes, but only if you lose the wallet itself or its recovery phrase. Always back up your recovery phrase securely and keep your hardware wallet in a safe location.
Take Action to Secure Your Cryptocurrency Today
Cryptocurrency security is a constant process. By following the steps in this guide—using hardware wallets, enabling 2FA, avoiding phishing scams, and conducting regular audits—you’ll greatly reduce your risk of losing your assets. Stay proactive, stay informed, and secure your cryptocurrency before it’s too late.
The Crypto Security Checklist is now available as a downloadable PDF. You can download it for printing from the link below:
Download Crypto Security Checklist
How to Use the Checklist
- Print or save this checklist for quick reference.
- Review each step regularly to ensure ongoing security.
Adrian Smith is a Web3 strategist and lead writer at CryptoBrandHub.com, with 8+ years of experience in crypto marketing, NFT monetization, and DeFi tools. He helps creators and investors navigate the fast-changing world of blockchain with practical, research-backed insights.

